AnyDesk Confirms Compromise of Code Signing Certificates
On 2 Febuary 2024, AnyDesk Software GmbH, the maker of the popular remote desktop software by the same name, disclosed that their corporate network had been breached and source code had been accessed and code signing certificates had been compromised. This was following a 4 day outage in which their software was inaccessible.
In their statement on 2 Febuary, AnyDesk claims that their remediation actions are complete and that “To date, we have no evidence that any end-user devices have been affected. We can confirm that the situation is under control and it is safe to use AnyDesk.”
For our purposes, this is not a sufficient statement to take on faith alone and until details of the timeline of the breach are confirmed and disclosed, we suggest assuming that AnyDesk certificates were compromised prior to this weeks outage.
What are the Implications of this breach?
The theft of code signing certificates means that malicious actors would be able to create malware signed by AnyDesk or trojanize AnyDesk clients and sign them to show they are legitimate. They could then use this as allowed malware for persistance that bypasses antivirus, antimalware, and application whitelisting controls.
Even after the code signing certificate is revoked, this software will still run on most systems so its’ important to update your AnyDesk installations and security analysts should hunt for any software using the revoked certificates.
At this time, AnyDesk denies, and there is currently no evidence to suggest, a supply chain compromise of AnyDesk customers through their software.
Timeline
Starting on 29 January 2024, AnyDesk suffered an outage lasting 4 days. During this time, they silently updated their software exchanging the old code signing certificate.
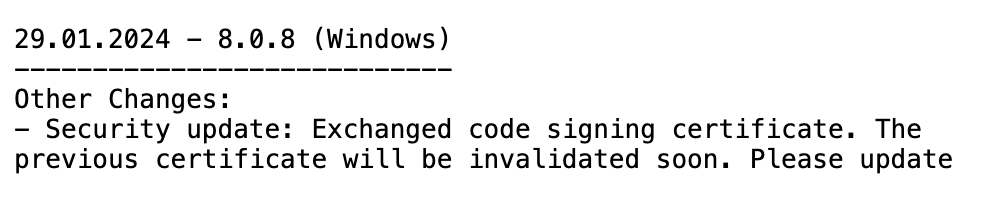
Code Signing Certificates are notably difficult to obtain and rarely swapped unless they expire or are considered compromised so there had been some chatter online of a possible breach. AnyDesk has since confirmed that this outage and the changed certificate were related to the breach.
Kaseya Customer Exposure
Kaseya Labs primarily reviews and reports on vulnerabilities affecting Kaseya customers. Among customers subscribed to our security monitoring services, we found thousands of customer networks running vulnerable versions of this application across many thousands of hosts making this a very high priority.
Recommendations
Customers are advised to shutdown these services until the patch can be applied. AnyDesk stated that they revoked all passwords to their web portal, my.anydesk.com, and they recommended that users change their passwords if the same credentials are used elsewhere.
Although AnyDesk has claimed they found no evidence of end-customer exposure, we advise you to review logs to determine if any malicious actions have taken place on any essential systems.
Threat Hunting should consist of looking for compromised certificates on any running applications. Using EDR you can search for the following indicators:
Signature Subject Name: 'AnyDesk Software GmbH'
Signature Issuer Name: 'DigiCert Trusted G4 Code Signing RSA4096 SHA384 2021 CA1'
Signauture Serial: '646F52926E01221C981490C8107C2F771679743A'
Yara Signatures have been published by security researcher Florean Roth here:
https://github.com/Neo23x0/signature-base/blob/master/yara/gen_anydesk_compromised_cert_feb23.yar
NOTE: Finding the legitimate vulnerable software is not evidence of a security incident of your own, simply a signal to update that software. The real threat is finding rogue malicious software signed with the compromised AnyDesk certificates. Vulnerability Info
- Product: AnyDesk
- Affected Versions: Prior to 8.0.8 (on Windows)
- CVE: N/A
- Type: Stolen Certificates
- Disclosure/Publish Date: 2 Febuary 2024
- Advisory: https://anydesk.com/en/public-statement
- First Patched Version: 8.0.8 (29 January 2024)
- First Exploited: Unknown
- First Publicly Available Exploit: Unknown



