WinRAR Actively Exploited – Patch Now
by Mike Puglia
3 min read
A WinRAR vulnerability published (CVE-2025-8088) which allows attackers to execute arbitrary code by crafting malicious archive files. This vulnerability actively being exploited in the wild and was discovered by Anton Cherepanov, Peter Košinár, and Peter Strýček from ESET. WinRaR does NOT have auto-update patching capabilities, meaning interaction by users or IT is required to remediate this vulnerability. Organizations should manually patch and update to version 7.13 or higher.
WinRAR is a commonly used compression/archive/extractor tool used to create and extract ZIP or RAR archives. In 2023 a similar WinRAR vulnerability was widely exploited by attackers due to its large install base within SMBs and MSPs.
Currently, we are seeing only 5% of systems have updated WinRAR to 7.13.
Vulnerability Information
- Product: RARLAB WinRAR
- Affected Versions: 7.12 and prior versions (fix is 7.13)
- CVE: CVE-2025-8088 (CVSS 8.4)
- CVE Publish Date: 8 August 2025
- Type: Local Code Execution via Path Traversal Vulnerability
- Advisory: https://www.win-rar.com/singlenewsview.html?&tx_ttnews%5Btt_news%5D=283&cHash=ff1fa7198ad19261efb202dafd7be691
- First Patched Version: 7.13 (https://www.win-rar.com/whatsnew.html)
- Status: Actively Exploited

Description: WinRAR versions 7.12 and earlier has a vulnerability that allows an attacker to create an archive that, when the user extracts it, can write arbitrary files to sensitive locations – such as the Windows Startup folder – allowing malware to be executed on the next restart.
In the wild, attackers have been observed sending phishing emails with zip/rar attachments that exploit this vulnerability when the user extracts the file contents using WinRAR. The user is shown a legitimate document to lower suspicion while the malicious file is silently written.
Our Response
Datto EDR and RocketCyber Managed SOC both have deployed rules to detect the misuse of WinRAR and their customers will be notified if an exploitation occurs.
Recommended Actions
Using Datto RMM
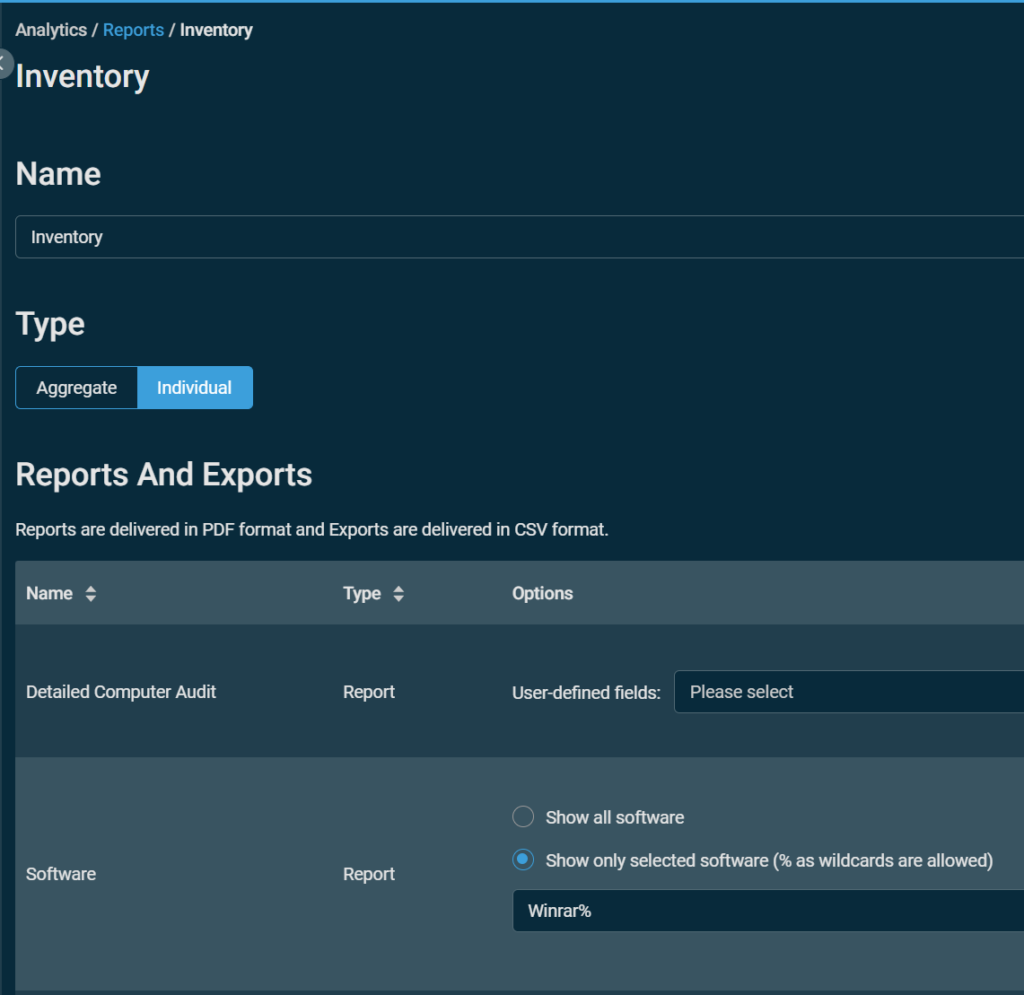
Run an inventory in your RMM to find vulnerable versions. As an example, Datto RMM users can find a software inventory report within Analytics / Reports / Inventory:
Using VSAX
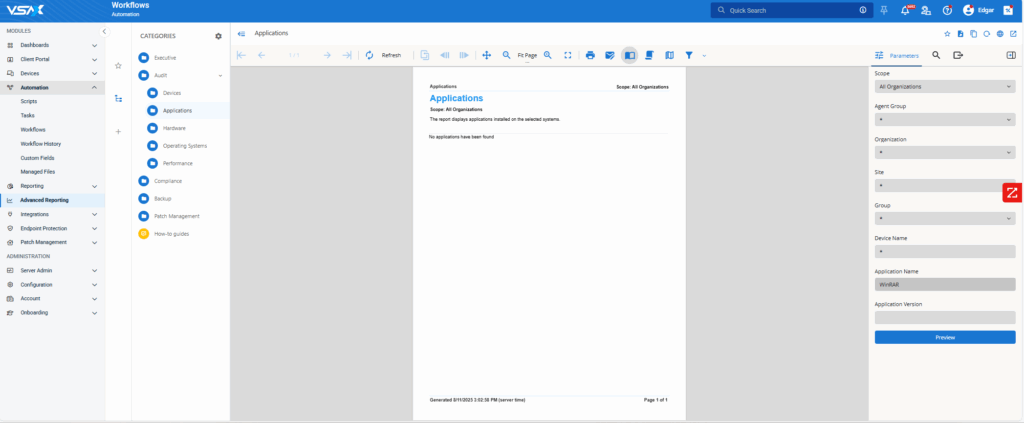
Run a report by going to Advanced Reporting ->Audit -> Applications and filter by Application Name – WinRAR:
Using Security Tools
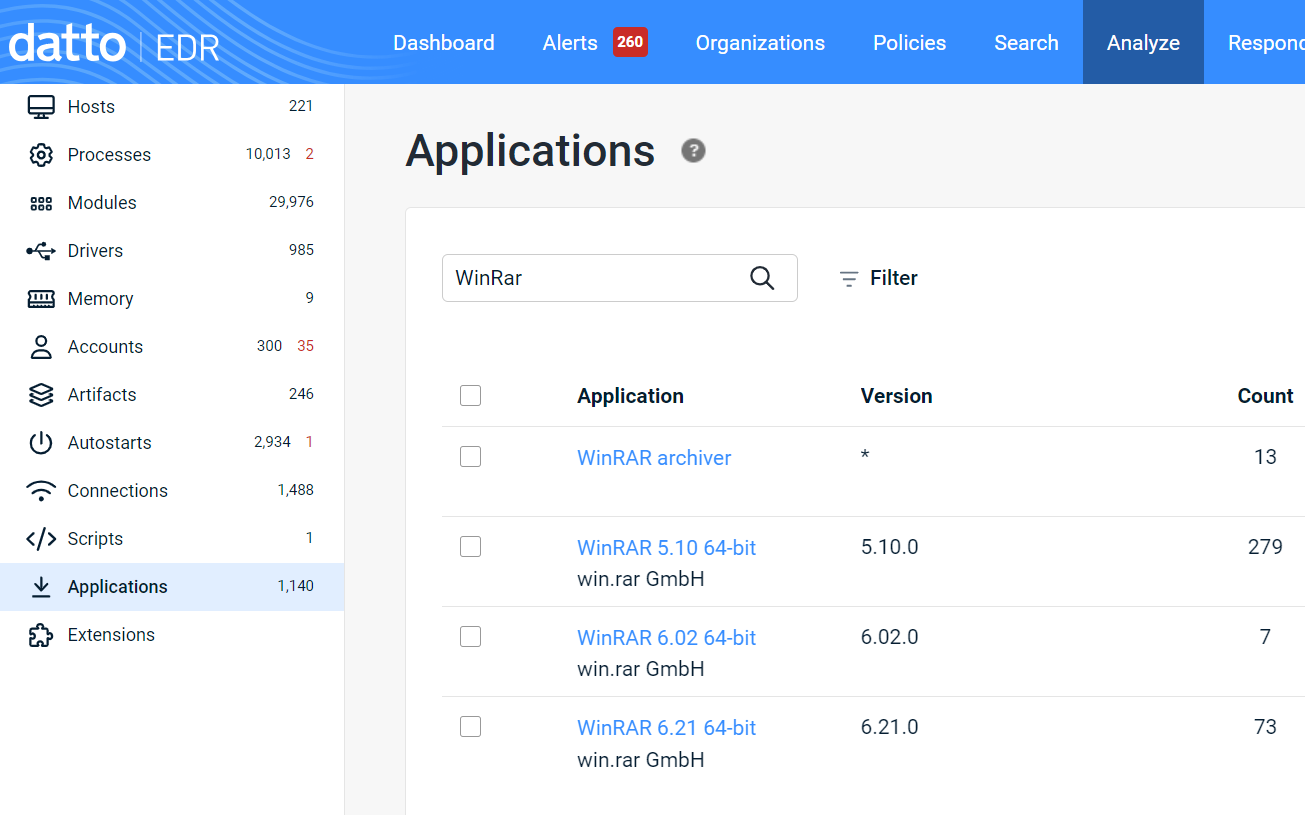
Vulnerability Scanners and EDR products often collect installed software version information. Within Datto EDR you can find installed application versions within Analysis:Applications or Search:Applications.
Using Powershell
You can also find vulnerable versions by running the following powershell command on your systems:
> Method 1 (Local):
Get-WmiObject -Class Win32_Product | where name -match WinRar | select Name, Version> Method 1 (Remote):
$dnsname = "workstation1.kaseya.internal"
Get-WmiObject -Class Win32_Product -ComputerName $dnsname | where name -match "WinRar" | select PSComputerName, Name, Version> Method 2 – Query Registry
$InstalledSoftware = Get-ChildItem "HKCU:\Software\Microsoft\Windows\CurrentVersion\Uninstall"
foreach ($obj in $InstalledSoftware) { "$($obj.GetValue('DisplayName')) $($obj.GetValue('DisplayVersion'))" } Additionally, the following Powershell script will check the version and update WinRAR to 7.13 if it is installed and running 7.12 or earlier (Please review the script in detail prior to running in a production environment as it will make changes to an installed application):






