Threat Bulletin: Akira Ransomware – Evidence & TTPs
by Billy Austin
5 min read
Executive Summary
Akira ransomware continues to target Windows, Linux, and ESXi systems. Over the past few weeks, the Kaseya SOC has seen an uptick in another version of Akira. Campaigns include destructive steps such as wiping recovery options, clearing event logs, and forcing victims into Tor-based negotiations. Below are the decoded evidence artifacts, encryption attributes, opcode discoveries, and historical indicators gathered across variants.
Static Analysis & Variants (Past Two Years)
Over the last two years, Akira has evolved from classic C++ Windows builds into Rust-based cross-platform variants. Static analysis of known samples reveals both consistent family traits and evolving techniques:
- Common ransom notes: akira_readme.txt, powerranges.txt – Persisted across variants, strong family marker.
- File extensions: .akira, .powerranges, .akiranew – Early C++ builds focused on .akira; Rust-based encryptors expanded with new extensions.
- Multi-platform support:
- Windows: C++ builds, sometimes packed (UPX/custom), with embedded shadow copy wipe commands.
- Linux/ESXi: Rust-based “Akira_v2” and “Megazord” builds, targeting /vmfs/volumes and ESXi management tools.
- Consistent anti-recovery techniques:
- Deletion of shadow copies (vssadmin, wbadmin, PowerShell WMI/CIM calls).
- Event log clearing via PowerShell and direct .NET APIs.
- Negotiation infrastructure: All variants direct victims to .onion portals with unique access codes for negotiation. Infrastructure domains rotate, but the Tor model has remained stable.
Research Hashes (Akira Samples)
- a99266340fb6880f8e0a8744b23a8b03
- 912e47abeab206fa01e646614be4594a
- b163803130f466db74f68a19f9cee11e
Common Obfuscation Tricks Observed
Akira samples frequently employ obfuscation to evade static detection. The most common methods include:
- Use of packers: Windows builds with UPX or modified packers to hide strings until runtime.
- Encrypted configuration blobs: Notes and URLs decrypted only at runtime.
- Runtime API resolution: Dynamic API loading hides sensitive calls from static inspection.
- Rust complexity: Large opaque binaries that resist easy reversing.
- String obfuscation: XORed, UTF-16, or otherwise encoded critical strings.
Why This is Important: These techniques make purely static YARA signatures less reliable. Defenders should pair static rules with behavioral detections (process command lines, shadow copy deletion, event log clearing) and consider unpacking/memory scanning during analysis.
Evidence and Importance
PowerShell Shadow Copy Deletion
Evidence: powershell.exe -Command “Get-WmiObject Win32_Shadowcopy | Remove-WmiObject”
Importance: Removes the ability to recover the machine to a known good state. Maps to T1490 – Inhibit System Recovery
Event Log Clearing (UTF-16LE Decoded)
Evidence: Get-WinEvent -ListLog * | ForEach-Object { [System.Diagnostics.Eventing.Reader.EventLogSession]::GlobalSession.ClearLog($_.LogName) }
Importance: Hides attacker activity (“cover their tracks”) making it more difficult to understand the compromise (slows forensics, recovery, etc…). Maps to T1070.001 – Clear Windows Event Logs
Encryption Attributes
Evidence: Notes (akira_readme.txt), extensions (.akira, .powerranges, .akiranew), multi-platform builds.
Importance: Family-level triage markers and strong forensic identifiers used to identify APT or Ransomware Group.
TOR Ransom Portal & Access Code
Evidence: https://akiralkzxzq2dsrzsrvbr2xgbbu2wgsmxryd4csgfameg52n7efvr2id[dot]onion Example access code: 9288-HR-HLEJ-CAYG
Importance: Reliable IOC for negotiation channel tracking.
Screenshot Evidence of the Analysis
1. Shadow Copy Deletion Command
Screenshot of the decoded PowerShell command:
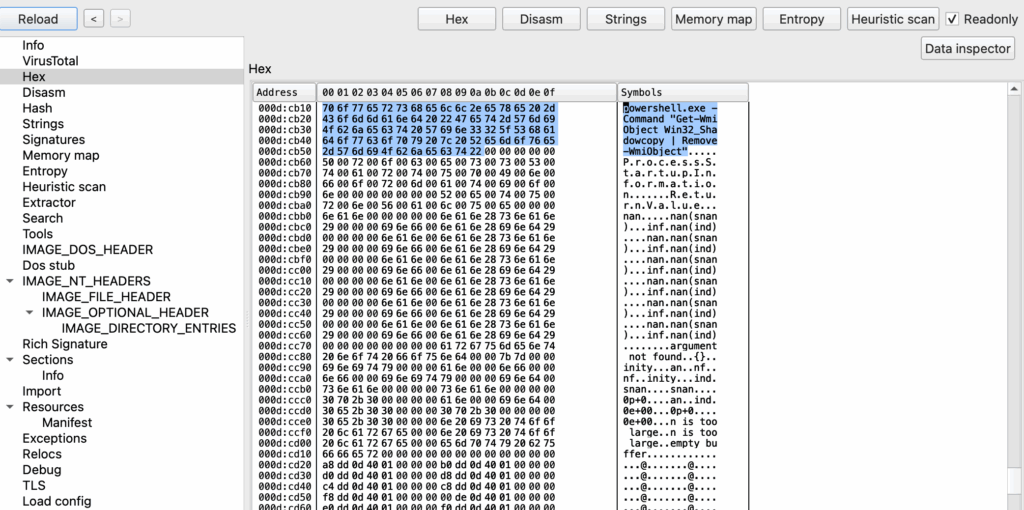
Demonstrates how Akira inhibits system recovery by deleting Volume Shadow Copies.
Mapped to ATT&CK T1490
2. Event Log Clearing via Get-WinEvent
Screenshot of the UTF-16LE decoded string:
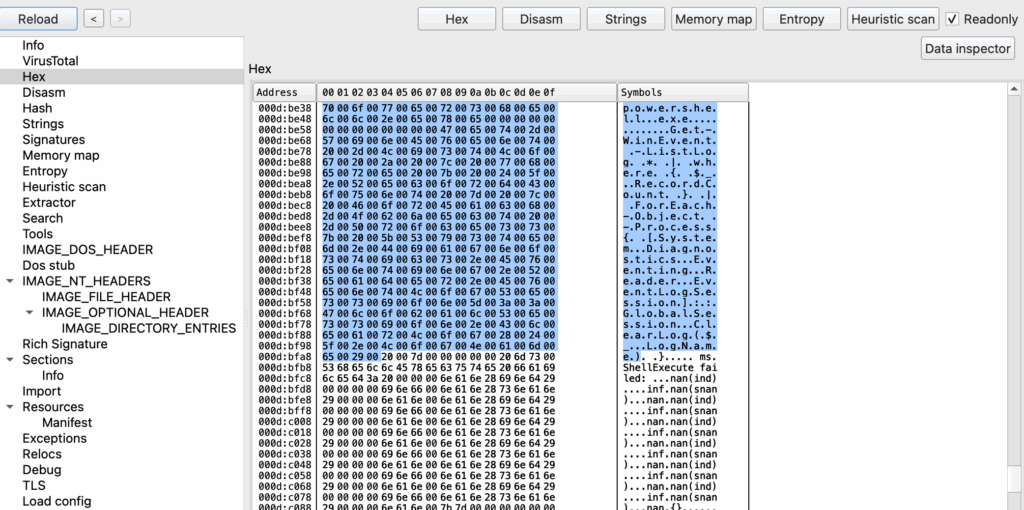
Shows Akira’s anti-forensics technique of wiping all event logs.
Mapped to ATT&CK T1070.001
Opcode Discoveries
Static disassembly of Akira binaries revealed consistent low-level opcode patterns used for malicious behavior:
Direct System Call Wrappers
– mov eax, <syscall#> → syscall stubs.
– Importance: Bypasses API monitoring hooks to avoid detection
Inline AES/ChaCha20 Rounds
– Opcodes like pxor, pshufd, aesenc.
– Importance: Confirms encryption routine presence.
Manual API Resolution Loop
– Pattern: xor ecx, ecx → lodsb → hash API names → call eax.
– Importance: Indicates runtime function resolving.
PE Unpacking Stub (Windows)
– Memory allocation + decompression loops after UPX header.
– Importance: Confirms packed delivery.
Defender Tip: Opcode-level YARA rules can be fragile, but hunting for these patterns in memory dumps is effective when string-based detection fails.
MITRE ATT&CK Mapping
- Impact – T1490 (Inhibit System Recovery): Shadow copy deletion, backup catalog wipes.
- Defense Evasion – T1070.001 (Clear Windows Event Logs): Log wiping to obscure evidence.
- Impact – T1486 (Data Encrypted for Impact): Files encrypted with Akira extensions; ransom notes dropped.
- Defense Evasion – T1027 (Obfuscated Files or Information): Packers, encrypted configs, runtime API resolution.
Why This Matters
Each of the decoded artifacts ties directly to a step in the ransomware playbook:
1. Destroy backups (T1490).
2. Wipe logs (T1070.001).
3. Encrypt files and drop ransom notes (T1486).
4. Tor portal for negotiation.
5. Obfuscation to evade static analysis.
6. Opcode signatures confirm encryption routines, API evasion, and unpacking behavior.
7. Screenshots provide visual forensic evidence for SOC and IR teams.
Together, these indicators provide defenders with actionable detection opportunities across process command lines, filesystem IOCs, opcode-level analysis, and network destinations. Both RocketCyber and Datto EDR include coverage for these threat artifacts.






